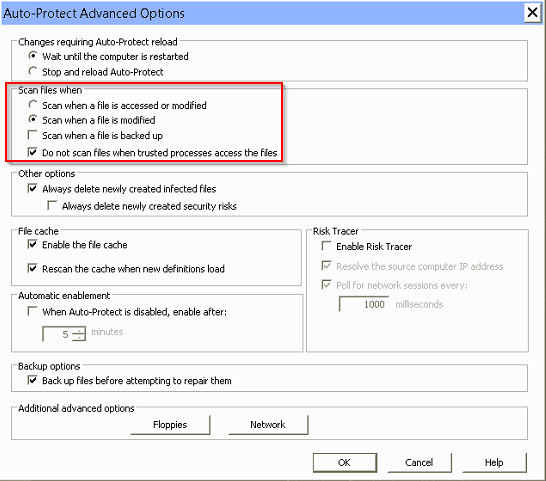
We had a customer who was experiencing slowness on their terminal servers and the slowness was keeping some reports in their core banking application from running. We found that when we excluded the entire C: drive of the terminal server from all Symantec Endpoint Protection scans, the errors would not occur. Through trial and error, we tracked down the setting in SEP that was causing the performance problems. We changed the “Scan files when” setting from “Scan when a file is access or modified” to “Scan when a file is modified”. This solved the performance issues and reports in their core banking application are running properly now.