Whether you work from home full-time, go to the office a couple of days a week, or work full-time in the office, each of us has adjusted our routines to deal with this new lifestyle. With these adjusted routines, it is imperative that we check in on our security routines to ensure the safety of our information and customer information. Some of the tactics we have relied upon in the past can still be helpful to us today, even if our routines look different.
So, what does it mean to "check-in" on our security routines? Consider these questions:
- What kind of habits make up a security routine?
- How can I monitor these habits and controls for myself and my employees as we encounter different types of risk every day?
- Is there guidance I can turn to for extra tips?
Change Passwords Frequently
Many organizations have implemented policies that force passwords to be changed on some sort of frequency to prevent fraudulent logins. Even if an account you use doesn't have this type of policy in place, consider updating passwords for your frequently used accounts to ensure further security.
Don't Share Passwords
If you're an administrator, manager, or officer of some sort for your organization, you may have elevated administrative privileges for certain accounts. None of your passwords should ever be shared with anyone else, including those within your organization. This can lead to unauthorized access, misuse, alteration, and destruction of data.
Implement Multi-Factor Authentication
This is especially helpful for employees working from home who must access your organization's network over a VPN. Home networks are not always as secure as the network of your organization, and your employees should have to verify their identity before accessing the company network from a different location.
Schedule Regular Exercises / Tests
Testing your organization's response to downtime, closures, or inability to access information can be critical for those situations that occur in real life. Are your employees prepared for how to continue critical operations if there's a network outage, or if they cannot report to their normal job site? Documenting these procedures in a business continuity plan is a start, but executing those procedures helps you identify gaps and areas that need improvement.
Schedule Annual Security Awareness Training
Improperly trained employees pose a large security risk to your institution. Even employees with low-level access to secure information should be trained to understand the importance of keeping information secure, and how to easily detect and report problems. Everyone at your institution plays a role in keeping customer and internal information secure, and creating an environment where risks can be taught, discussed, and used for educational purposes is vital. At least once a year, enroll all employees in security awareness training. As part of the security awareness training, conduct simulated phishing tests. If certain employees continuously fail your simulated phishing tests, take that as an indication that additional security awareness training is needed.
What are my next steps?
As you check in on your security routine, remember that you can always refer to guidance for additional tools and verification. Checking in on your security routine not only benefits your own knowledge and skills, but it benefits the overall well-being and security of your information, so your organization can continue to thrive and provide exceptional service.



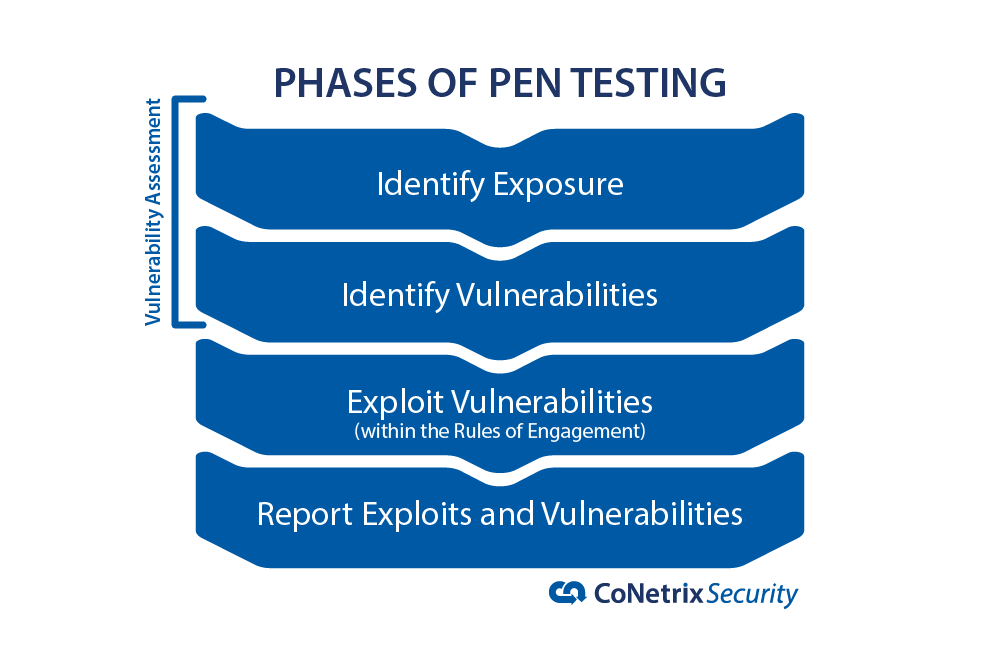 One of the best things you can do when evaluating a pen test company is ask them for examples of what they have done. See how they did it and whether you're comfortable with the things they are capable of doing.
One of the best things you can do when evaluating a pen test company is ask them for examples of what they have done. See how they did it and whether you're comfortable with the things they are capable of doing.