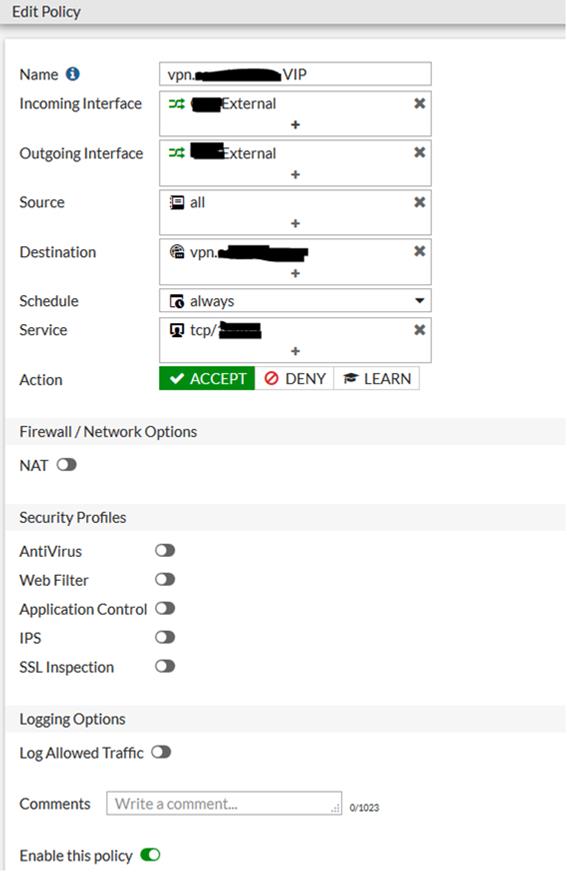
When a secondary public IP address is utilized for VPN connections, the configuration of an IPSEC VPN versus an SSL VPN is quite different. For an IPSEC VPN, it's as easy as turning flipping a switch and selecting the IP address:

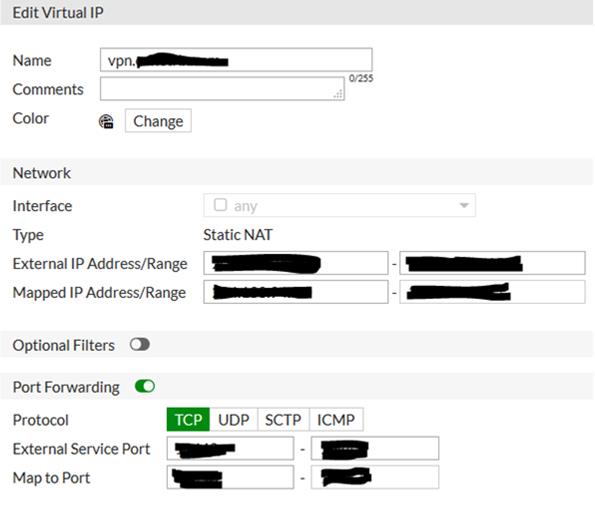
For SSL VPN it takes a couple of steps: First a Virtual IP (VIP) has to be created that points the primary IP at the secondary IP. Additionally include port forwarding for the SSL port to be utilized:
Second, an IPv4 policy needs to be created using the WAN interface for both incoming and outgoing, with the destination being the VIP: