Identity Theft Prevention Program Tool
On November 9, 2007, the Agencies jointly issued final rules and guidelines to implement Sections 114 and 315 of
the Fair and Accurate Credit Transactions Act of 2003 (FACT Act). These rules require financial institutions
(banks, credit unions, trust companies, mortgage companies) and creditors to develop and implement a written
Identity Theft Prevention Program to detect, prevent, and mitigate identity theft in connection with covered
accounts. Additionally, the rules require financial institutions to establish policies and procedures to assess
the validity of a change of address.
CoNetrix offers online software to help create your Identity Theft Prevention Program document, along with
customizable employee training for Identity Theft Red Flags. Our software follows the FDIC, OCC, FRB,
NCUA, and FTC (the Agencies) red flag rules and guidelines and enables you to efficiently create a complete
Identity Theft Prevention Program.
Red Flags Risk Assessment
Use your program details to inform the development of an identity theft risk assessment for each covered account.
Based on known red flags and your organization's history with identity theft, document the likelihood and potential damage of a covered account being opened or accessed fraudulently.
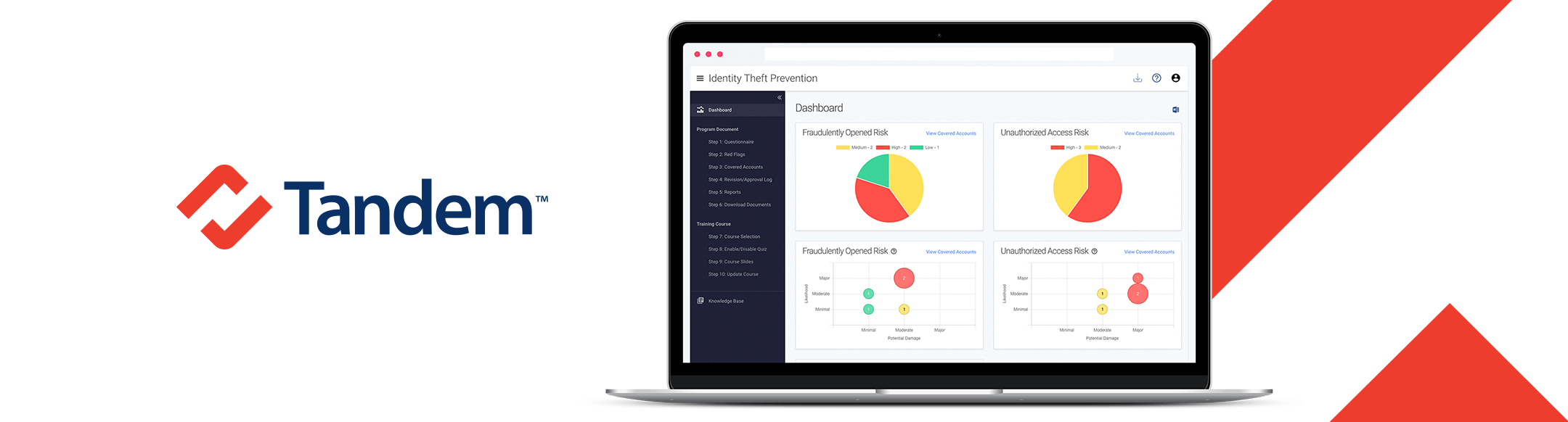
Dashboard
Review visual representations of your identity theft prevention program on a dashboard.
Evaluate useful insights into your red flags risk assessment, as well as a series of reports, designed to ensure your program does not contain any missing or incomplete data.
Training Course
Develop and distribute an identity theft training course, based on the red flags and covered account details in your program.
Enroll an unlimited number of employees in online training and generate reports to show training completion and effectiveness.
Downloads
Export your identity theft prevention program data in a variety of ways, including the full program document for your senior management, auditors, and examiners; an annual report template for the board of directors; and red flag checklists for your employees to reference while they are on the job.
These customizable documents are available in Microsoft Word and Adobe PDF formats.
The Tandem Identity Theft Prevention Program software includes the ability to:
- Work through an easy multi-step process to create your program
- Update your information annually
- New features and updates are automatically included with your annual subscription
- Download your program in an editable Microsoft Word document or as an Adobe PDF
- Utilize a red flags training course, based on your red flags and covered accounts
- Modify the course's content
- Manage and enroll an unlimited number of users in red flag training
- Obtain reports to show who has taken and passed the training
- Download the red flags training as a Microsoft PowerPoint presentation
Features
The CoNetrix Tandem Identity Theft Prevention Program software is feature-rich, including:
- An online framework created and updated by security and compliance experts
- Free training workshops to help familiarize you with the software
- Integration with other CoNetrix online software
- Anywhere/anytime Internet access through a secure, online portal
- Multi-factor authentication
- Single Sign On (SSO) integration using SAML 2.0
- Multi-user access
- No software installation or equipment costs
- The ability to manage several companies' programs with one login (requires a subscription for each company)
Identity Theft Red Flag Links